

Cite As: Edward
A. Cavazos and Coe F. Miles, Ph.D., Copyright on the WWW: Linking and Liability,
4 RICH. J.L. & TECH. 3, (Winter
1997) <http://www.richmond.edu/~jolt/v4i2/cavazos.html>[**].
{1} The World Wide Web (WWW) is so often used as a way of interacting with the Internet that many people mistakenly confuse the two, referring to the Internet as the "Web" and vice versa. Of course, the Internet and its native applications predate the development of the WWW protocols by decades.[2] Still, given the overwhelming amount of available Internet bandwidth now devoted to the transmission of web pages, there is no doubt that the WWW is the interface of choice for most users of the world's most pervasive computer network.[3] The WWW is not the Internet, but there can be no doubt that it is the Internet's first "killer app."[4]
{2} Simply put, the WWW is a set of protocols that facilitates access to geographically dispersed data via a multimedia graphical user interface. When a user peruses material made available via these protocols (a process called "browsing"), references to related material on the WWW might be presented as "links." These links allow the user to access the referenced material, which may contain links of its own. So, for instance, a footnote in an article published on the WWW might not just provide a citation to a related article, but might, if selected, actually display the source material in its entirety. It is linking that makes the WWW web-like, with documents seamlessly referencing and cross-referencing each other. The result is that browsing the WWW differs fundamentally from traditional means of research, in that it is inherently non-linear. Users can jump from one document to another, following a unique course on an indirect pathway through cyberspace.
{3} However, WWW linking raises some interesting legal questions. Does the provision of a link implicate intellectual property rights? Is there potential liability which attaches for unauthorized linking? This paper addresses these and related questions. In part II, we examine the nature of the WWW protocols and explain what actually happens in the process of linking. In part III, we describe some interesting real-world fact patterns that highlight some of the unique intellectual property issues that can arise on the WWW. Part IV is a review of copyright principles in light of the WWW and the unique linking problems previously identified. Part V discusses some possible defenses to copyright infringement claims based on linking. Finally, in Part VI, we briefly explore intellectual property doctrines other than copyright that might come into play.
{4} Documents on the WWW are encoded pursuant to a set of standards called HyperText Markup Language, or HTML.[5] HTML documents are text files containing content text (i.e., the information to be displayed to a user) and HTML instructions. Programs called "browsers"[6] are applications that interpret[7] the HTML instructions in a marked-up document and, in accordance with these instructions, display the document's content to the user. Many HTML instructions denote special formatting for the content text. For instance, in an HTML encoded document, the command <B>Hello!</B> directs the user's browser to display the text "Hello!" in bold text. Other HTML instructions coordinate the placement of tables or forms amidst the content text.
{5} Some HTML instructions are used to identify/locate other hypertext elements. These instructions are referred to as "links." Links are often, although not exclusively, denoted by emphasized text or by "clickable" icons. When a user selects a link, the user's browser program interprets the HTML instruction associated with that link to locate, retrieve, and process the link's target. The target might be another HTML document, an image, a video segment, an audio file, or some combination of these elements.
{6} For purposes of this paper, we identify two generic classes of links (local and remote) and two link attributes (invoke-to-load and auto-load). Local links are links in one HTML document (the parent document) that refer to a document or element stored at the same physical site as the parent document. Remote links are embedded in the parent document and point to a document or element stored at a site other than that where the parent document resides. Invoke-to-load links require a user to affirmatively select or invoke them before the link's target is located and displayed. Auto-load links are invoked automatically by the user's browser when the parent document containing the link is displayed. Auto-load links are typically used to display images "in-line" with the parent document's text, giving the appearance that the image is a "part of" the parent document.
{7} Either attribute can be applied to either class of link, making four types of links possible: (1) local invoke-to-load, (2) local auto-load, (3) remote invoke-to-load, and (4) remote auto-load. For example, in a WWW rendition of a newspaper article, an accompanying photograph might be displayed by an auto-load link to an image file. Since it is of the auto-load variety, the link will instruct the user's browser to pull up the image automatically when the article's text is displayed. The result of an auto-load link like this is often referred to as an "in-line image." If the image is stored on the same computer as the article's text file, then the link is a local link. If the image is stored elsewhere, then the link is a remote link. Other related photographs might be indicated on the page by invoke-to-load links. To see these, the user would have to manually click on an icon or highlighted text indicating their availability. Again, these might be locally or remotely stored.
{8} In addition to understanding the distinction between different types of links that might be implemented in a given WWW page, it is important to understand some other interesting technical characteristics of the WWW. First, HTML documents are strictly limited to plain (ASCII) text. They do not contain images, sounds or other non-textual elements. In order for an image to be displayed concurrently with the document, a link to the image element (either local or remote) is necessary. Even somewhat simple web pages, then, might contain a large number of links to elements that make up the page's formatting.
{9} Second, links only identify the location of a target element, such as an HTML document or an image, and are not the element themselves. Embedding a link in an HTML document is not the same as actually placing the element in the document. Third, it is the user's browser that interprets the HTML instruction identified by the link. So, when the browser encounters a link, it initiates the network connection to the referenced element, facilitates the transmission of a copy of the element to the user's computer, and then processes the element so that it can be appropriately displayed (or, in the case of an audio file, heard).
{10} Recently, some interesting fact patterns have emerged that pose fundamental questions about the legal implications of linking. Two particularly intriguing situations are worthy of examination in that they highlight how quickly legal issues involving linking can become complex.
{11} The popular Dilbert comic strip chronicles the experiences of Dilbert, a corporate drone who is faced with the bureaucracy and mediocrity of the modern workplace. United Feature Syndicate, Inc. (UM), copyright owners of the Dilbert comic strip, maintain an Internet website where users can view recent Dilbert cartoons, purchase Dilbert related products, and contact either UM or the comic's author, Scott Adams.[8] In January 1996, a Princeton University graduate student[9] created a WWW site he called the Dilbert Hack Page[10] (DHP) which allowed users to view recent Dilbert comics in a context different from that provided by UM.
{12} The DHP used the names of Dilbert comic image files, obtained from the UM Dilbert site each day, to generate a remote auto-load link that was written into the DHP's HTML document (as ASCII text). When visitors to the DHP subsequently downloaded (browsed) the DHP's HTML document to their computer, the remote auto-load link HTML instructions were interpreted by the user's browser which, in turn, contacted UM's Dilbert site, downloaded the links' identified image files, and displayed the targeted image files. See Figure 1.
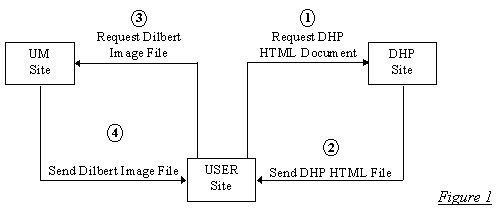
{12} For analytical purposes, it is important to note that the DHP HTML page did not contain the subsequently displayed Dilbert image files. The DHP's author never duplicated the Dilbert cartoons at all. What the DHP HTML page did, however, is identify the precise location (computer site and file name) of the targeted Dilbert image files and, based on this information, the image files were obtained directly from UM's Dilbert site by the user's browser for incorporation into the DHP as displayed on the user's computer. In July 1996, UM contacted the DHP's author informing him that Dilbert comic strips were the intellectual property of UM and could not be used without their express written consent.[11] A subsequent letter by UM's legal counsel alleged the DHP was a clear copyright violation and threatened legal action.[12] In the face of an uncertain liability, the DHP was removed from active service in August 1996.[13]
{13} Another intriguing fact pattern involves a web-based news clearinghouse called TotalNEWS.[14] TotalNEWS uses frame technology[15] to display content from a number of different news sources while the user continues to see the TotalNEWS Logo and associated advertisements. Through frames, TotalNEWS divides a browser's window into four separate regions as shown in Figure 2. Region 1 contains a number of links to news sources such as CNN®, CBS®, and USA Today®. Region 2 contains a logo that alternates between TotalNEWS' logo and that of an advertiser. Region 3 contains content; when a user selects one of the links in region 1, information from that news provider is displayed in region 3. Region 4 contains an ever changing assortment of advertisements.[16]
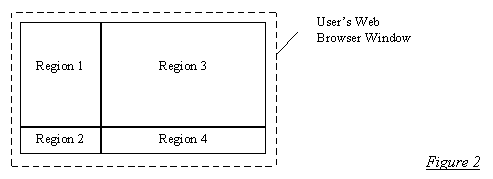
{14} TotalNEWS' use of frames in this manner allows the site's administrators to display their logo (and advertisements) while simultaneously displaying the content from other unaffiliated sources. Unless the targeted content provider (e.g., CBS®) prominently displays its logo or other identifying mark in each portion of information it provides, users browsing TotalNEWS' website could be confused as to whose information they are viewing. In February 1997, a number of news entities to whom TotalNEWS was linking filed suit alleging, among other things, copyright and trademark infringement and that their content is being passed off (at least to some users) as that of someone else.[17]
{15} In June of 1997 the parties entered a stipulation[18] that required defendant TotalNEWS to "cease the practice of 'framing' Plaintiffs' websites"[19]except via plain text links.[20] As we argue later,[21] it appears that TotalNEWS would not be liable under copyright law, but is nonetheless bound by its stipulation with Plaintiff news organizations.
{16} Under the present incarnation of the copyright act[22] (hereinafter referred to as the Act), copyright adheres instantly in "original works of authorship fixed in any tangible medium of expression."[23] Since original "means only that the work was independently created by the author . . . and that it possesses at least some minimal degree of creativity,"[24] and a work is "fixed in a tangible medium of expression when its embodiment . . . is sufficiently permanent or stable to permit it to be perceived [or] reproduced . . . for a period of more than transitory duration,"[25] it would appear that virtually all WWW publications are eligible for copyright protection[26]
{17} Benefits of copyright spring from the Act's grant of exclusive rights to the copyright owner.[27] The Act recognizes six exclusive rights: (1) reproduction,[28] (2) preparation of derivative works,[29] (3) public distribution, (4-5) public performance or display[30] and (6) public performance via digital audio transmission.[31] These rights may be exercised directly by the author or through third parties via assignment or license.[32] They may even be exercised in the negative, through the prohibition of all uses.[33]
{18} Notwithstanding the grant of broad rights provided the copyright owner in Section 106, Sections 107 through 121 of the Act set forth a number of specific limitations.[34] Further, case law tells us that one cannot obtain a copyright on facts,[35] information in the public domain,[36] scenes of faire,[37] cliché language and metaphors.[38]
{19} To be held liable under copyright principles, the party creating a link to the copyrighted material (hereinafter, the "linking party") must qualify as either a "direct infringer" or some sort of "contributory infringer." It is important, then, to understand the differences between these two doctrines before analyzing the scope of link-related liability.
{20} The Act provides that "[a]nyone who violates any of the exclusive rights of the copyright owner is an infringer."[39] Two elements must be established to prove infringement: (1) ownership of a valid copyright, and (2) copying of constituent elements of the work that are original.[40] Importantly, the Act does not require intent on the infringer's part.[41] If a party's acts are sufficient to satisfy these two elements, then that party is considered a "direct infringer" and is subject to liability.[42]
{21} Of particular interest here is the effect a single act on the WWW (e.g., browsing a home page) has on the copyright owner's enumerated rights.[43] The act of retrieving documents or HTML elements on the WWW might implicate a variety of the enumerated rights in somewhat different ways depending on the circumstances.[44] For instance, the Ninth Circuit has held that the requisite "copying" for infringement purposes can occur when a computer program is transferred from permanent storage to a computer's Random Access Memory (RAM).[45] Other courts have extrapolated this fundamental rule and found that an "upload or download" of a computer file from a remote computer system similarly qualifies as the type of copying that implicates the author's exclusive rights.[46]
{22} Also potentially implicated when WWW materials are perused are the display,[47] public distribution,[48] and derivative[49] rights. In Mirage Editions, Inc. v. Albuquerque A.R.T. Co.,[50] the defendant removed artwork from purchased books, affixed the artwork to a tile, and resold the tile for commercial gain.[51] Without analysis, the Ninth Circuit found him liable for violating the copyright owner's right to make and authorize the creation of derivative works. In Lee v. Albuquerque A.R.T. Co.,[52] a case having virtually the same facts as Mirage, the Seventh Circuit concluded that the copyright owner's derivative right was not violated. The Lee court reasoned that merely bonding artwork to a tile was analogous to framing a picture, an act that does not change, recast, adapt, or transform the original artwork.[53] The court noted that to hold otherwise would be to make "criminals out of art collectors and tourists,"[54] and anyone else who frames a purchased artwork.[55]
{23} Under the guise of enforcing a copyright owner's derivative right, the Mirage court has, in effect, expanded an author's moral rights beyond those provided by statute. Specifically, the Copyright Act limits an author's moral rights to "prevent any intentional distortion, mutilation, or other modification of that work which would be prejudicial to his or her honor or reputation, and any intentional distortion, mutilation, or modification of that work is a violation of that right."[56] Even these rights are limited to "works of visual art" which is itself restricted to mean either a painting, drawing, print, sculpture or still photographic image, existing in a single copy, in a limited edition of 200 copies or fewer that are signed and consecutively numbered by the author.[57]
{24} Some courts have held that "authorizing" another's infringing conduct is itself a direct infringement.[58] But legislative history indicates that "[u]se of the phrase 'to authorize' [in 17 U.S.C. § 106] is intended to avoid any questions as to the liability of contributory infringers."[59] Not surprisingly, then, other courts, have expressed doubt as to whether 'authorization' constitutes a separate method of direct infringement.[60]
{25} Is there a direct infringing act during the linking process? A quick review of the scenarios discussed in Section II seems to indicate that, at least in circumstances similar to the one posed by the Dilbert Hack Page and the TotalNEWS service, the only possible direct infringer would be the end user. That is because the linking party is not doing anything that seems to involve a direct manipulation of the copyrighted materials at all. As one set of commentators note, "they [the linking party] do not perform an act of copying - the essential element for copyright infringement liability."[61] Because of the nature of the underlying technology, all of the acts that appear to be infringements (reproductions, distributions, and displays) are performed by the end user who is accessing the content directly. The linking party's only role in the process is the provision of information about how such access can be accomplished. This information takes the form of a Uniform Resource Locator (URL)[62] with which the user effectuates (via their browser program) the retrieval and manipulation of the copyrighted material.
{26} Even if a court were to take an expansive and liberal interpretation of the linking party's role and argue that the linking party was somehow taking the copyrighted work and manipulating it (which they are not), it seems that the only claim would be one similar to the one in Mirage. [63] However, the more persuasive Lee analysis seems to clear the linking party of any real concern.[64]
{27} While no court has yet been faced with a linking fact pattern, courts faced with the somewhat similar situation of computer bulletin board system operator liability have usually found that an intermediary system operator is not appropriately viewed as a direct infringer when the system's end users are the actors primarily responsible for direct manipulation of the copyrighted material.[65] Where courts have deviated from this finding, their reasoning is questionable.[66] Significantly, unlike the scenarios described here, the cases which hold that the system operator is not a direct infringer have involved situations where the copyrighted material is actually stored and processed on the system operator's computers. Nonetheless, the courts addressing these cases refrained from finding the system operators responsible for direct infringement.[67] It seems untenable for courts to hold linking parties liable as direct infringers for similar reasons, and the courts should turn to some other theory of liability as the source for copyright owners' relief.[68]
{28} Unlike federal patent law, the Copyright Act "does not expressly render anyone liable for infringement committed by another."[69] The absence of such express language in the copyright statute does not preclude the imposition of liability.[70] As defined by the Second Circuit, "[o]ne who, with knowledge of the infringing activity, induces, causes, or materially contributes to the infringing conduct of another, may be held liable as a 'contributory' infringer."[71] Importantly, there can be no contributory infringement unless there is an actual direct infringement by a third party.[72] Still, where a party is implicated in copyright infringement, yet has not precipitated the acts required for a direct infringement claim, contributory infringement may be the proper vehicle for assessing liability.
{29} Courts have recognized two types of contributory infringers: those who provide the means (usually a product) to infringe, and those whose physical conduct participates in or furthers the infringement.[73]
Means to Infringe
{30} One type of contributory infringement is "means to infringe" liability. For a means to infringe cause of action to accrue, the plaintiff must show (1) that the defendant knowingly created an instrumentality for infringing one or more of the owner's exclusive rights which (2) had no substantial non-infringing use, and (3) the existence of direct infringement. [74] If these elements are established, liability attaches regardless of either the amount of control the defendant has over the direct infringer or whether they have an economic interest in the infringing activity.[75]
{31} In the landmark case of Sony Corp. of America v. Universal City Studios, Inc.,[76] television program copyright holders alleged that the sale of video tape recorders (VTRs) allowed consumers to conduct illicit copying of television programs.[77] The plaintiffs argued that the VTR manufacturers should be held liable as contributory infringers since they (Sony, et al.) manufactured and marketed VTRs.[78] Borrowing patent law's test of substantial non-infringing use, the U.S. Supreme Court decided that the VTRs are capable of a substantial non-infringing use, and, therefore, the defendants should not be held liable for contributory infringement.[79] The substantial non-infringing use relied on by the Court was "time-shifting,"[80] which occurs when consumers tape a television program for viewing at a later date.[81] Although, at first glance, time-shifting seems to constitute a direct infringement by the consumer/viewer, the Court held that it was a protected fair use under the Copyright Act, and, thus, did not amount to infringement.[82] The dissent criticized the substantial non-infringing use test, arguing that only very unimaginative manufacturers could not delineate a substantial non-infringing use for most technologies, even if the technology was primarily designed for infringement.[83]
{32} How does this test play out for technologies other than video recorders? Some otherwise troubling scenarios become easy to analyze under the Sony test. For example, a library that makes photocopiers available to the public is clearly facilitating infringement in cases where library visitors use the copiers for illicit copying, but since the photocopier has substantial non-infringing uses, the library should not be considered a contributory infringer.[84] Courts have also applied the Sony test in the context of computer software. In Telerate Systems, Inc. v. Caro,[85] the court relied on the Sony test in holding a software manufacturer liable for contributory infringement.[86] The defendants' alleged primary non-infringing use was, in actuality, the main infringing activity.[87] However, in Vault Corp. v. Quaid Software Ltd.,[88] the Fifth Circuit used the Sony test in holding a software manufacturer not liable for contributory infringement on the basis that its program had substantial non-infringing uses.[89] The Vault court reached this conclusion even though the manufacturer conceded that it had actual knowledge that its product was used to make unauthorized copies of copyrighted material.[90]
Participatory Infringement
{33} Another form of contributory infringement is often called "participatory" infringement. For a participatory infringement cause of action to accrue, a plaintiff must show the defendant had (1) knowledge of a (2) direct infringement by another, and (3) induced, caused, or materially contributed to that infringing activity.[91]
{34} In Screen Gems-Columbia Music, Inc. v. Mark-Fi Records, Inc.,[92] the infringer violated plaintiff's copyrights on certain musical compositions by copying and reproducing an unauthorized album.[93] The plaintiff sued not only the organization who produced the album, but also an advertising agency for placing non-infringing advertisements for the sale of the infringing albums, a radio station for broadcasting such advertisements, and a packaging agency for shipping the infringing albums.[94] The court held that the advertising agency, the radio station, and the packaging agency could be liable for contributory infringement if they knew or should have known the infringing nature of the specific albums.[95] In Gershwin Publishing Corp. v. Columbia Artists Management[96], the defendant was a manager of concert artists and a creator and producer of local concert associations which provided audiences for its artists.[97] The court found the defendant liable for contributory infringement because the defendant knew that its artists included copyrighted compositions in their performances and that neither its local associations nor its performing artists had secured copyright licenses.[98] The court in that case described the defendant's activities as "pervasive participation"[99] and agreed with the lower court that the defendant "caused this copyright infringement."[100]
{35} The Ninth Circuit's recent opinion in Fonovisa v. Cherry Auction, Inc.[101] highlights how courts struggle with the parameters of the participatory infringement doctrine. In the lower court's opinion, a California Federal District Court discussed the issue of how much participation is needed to trigger contributory infringement.[102] The defendant was the owner of a swap meet at which independent vendors were selling counterfeit music tapes.[103] Although the district court accepted plaintiff's assertion that the defendant knew the illegal activities were occurring, it nevertheless held that the defendant's actions were passive and not substantial enough to constitute contributory infringement.[104] "Merely renting booth space is not 'substantial participation' in the vendor's infringement activities."[105] In addition, the district court noted that the plaintiffs failed to plead how the defendant acted "in concert with the vendors to accomplish the purpose or plan of selling counterfeits."[106] In reversing the District Court, the Ninth Circuit disagreed, holding that "providing the site and facility for known infringing activities is sufficient to establish contributory liability."[107]
The Linking Party as a Contributory Infringer
{36} Assuming, for the moment, that the end user's activities are deemed to be direct infringements,[108] does the linking party act in such a way as to satisfy the elements necessary to establish contributory infringement? In certain circumstances, it may. The relevant inquiry becomes: what type of link is involved? Arguably, where the linking party sets up a remote invoke-to-load link to copyrighted material on a Web page, it seems plausible that the linking party no more "participates" in or "materially contributes" to the acts of the user than the author of a traditional paper-based article who provides a footnote to a supporting authority or an entry in a bibliography.[109] Despite the Ninth Circuit's opinion in Fonovisa, recent opinions dealing with on-line service operator liability for a user's infringing acts seem to imply that simply providing the facilities through which infringement is committed is not the "substantial participation" needed to support a participatory infringement claim.[110] Here, the linking party seems to have even less involvement. Certainly, then, for an invoke-to-load link, at least, simply establishing the link seems equally unlikely to meet this threshold.
{37} If the link in question is an auto-load link, however, it may be the case that the link looks and functions more like a "means to infringe" or that the linking party so substantially participates in the user's acts that the linking party can be deemed a participatory infringer. The end user need not act at all here - his or her browser is directed to act by the HTML coding implemented by the linking party. This HTML code could very well be deemed a means-to-infringe. Also, the provision of this code approaches substantial participation in a way that providing an invoke-to-load link does not.
{38} The situation is muddied when it comes to framed sites like TotalNEWS where an invoke-to-load link results in a composite page on the user's screen that contains the copyrighted material as a constituent component. If the user's browsing is somehow deemed to be infringing, then the linking party responsible for the framed site runs the risk of liability as both a participatory infringer and for creating a means to infringe. Providing this type of link would seem even more likely to represent the requisite substantial participation in the end user's direct infringement for purposes of participatory infringement. Moreover, since the link would function as the "instrumentality" for the users' infringing act, it would likely be deemed a "means to infringe" as well. In none of the situations described thus far does the linking party have the opportunity to defend a means-to-infringe claim on the grounds that the link has substantial non-infringing use, as the only purpose for the unauthorized links in these examples is to act as an instrumentality for infringement.[111]
{39} If the act of setting up a link is, as we argue, not in and of itself an act that implicates the linking party in a direct infringement claim, then the only way the party might be found liable under the copyright law is under a theory of contributory infringement as described above. As noted, the contributory infringement doctrine requires that the end user (who performs the processes that implicates the Act) be deemed a direct infringer.[112] However, when one closely reviews the end user's activities in a WWW linking scenario, traditional defenses to infringement come into play that appear to obviate the end user's liability. This shields the linking party as well, since there is no direct infringement upon which to base the finding of contributory infringement. This is exactly what happened in Sony, where the court's determination that the consumer was engaged in fair use precluded a finding of contributory infringement on the part of the video tape recorder manufacturer.[113] In this section, we discuss two possible defenses, implied license and fair use, and contend that in an unauthorized linking situation, one or both will usually make it unlikely that the end user qualifies as a direct infringer, and thus the linking party is not properly viewed as a contributory infringer.[114]
{40} While a copyright owner can always sell or license his or her exclusive rights to third parties, Section 204 of the Copyright Act invalidates such a transfer of ownership unless it is in writing.[115] A transfer of copyright ownership is an "assignment, mortgage, exclusive license, or any other conveyance, alienation or hypothecation of a copyright or of any of the exclusive rights comprised in a copyright but not including a non-exclusive license."[116] Courts have recognized that this section assures that the creator of the work will not give away a copyright inadvertently and forces parties who want to use the work to negotiate with the creator to determine precisely what rights are being transferred and at what price.[117]
{41} The language of Section 101 specifically removes non-exclusive licenses from the writing requirement of Section 204.[118] Non-exclusive licenses occur where the licenser-owner of the work permits the use of the work in a particular manner without transferring ownership of the copyright to the licensee.[119] The existence of any license, whether exclusive or non-exclusive, creates an affirmative defense to a claim of copyright infringement.[120]
{42} It is well established that non-exclusive licenses may be granted orally, or may even be implied from conduct of the parties.[121] According to Nimmer, the existence of non-exclusive licenses "is not expressly provided in the statutory text, but is negatively implied from the fact that a 'transfer of copyright ownership,' which by definition does not include non-exclusive licenses must be by written instrument."[122] Thus, the copyright owner can grant a non-exclusive license (his consent to what would otherwise be an infringing activity) in the form of mere permission or lack of objection which is equivalent to a non-exclusive license and is not required to be in writing.[123] The Seventh Circuit has looked at Nimmer's pronouncement regarding the enforceability of non-exclusive copyright licenses and found that "Nimmer is right."[124]
{43} In order to determine whether such an implied non-exclusive license exists, every objective fact concerning the transaction should be examined to determine whether it supports such a finding.[125] Several objective inquiries can be made in this regard, including an assessment of whether the delivery of the copyrighted material was without warning that its further use would constitute copyright infringement.[126] It may also be instructive to turn to patent law, where courts have more fully developed methods for determining whether or not an implied license exists. An implied license to use a patent arises out of objective conduct by a party which a reasonable person can regard as indicating that some type of agreement has been reached.[127]
{44} Federal courts have used the implied non-exclusive license doctrine to defeat infringement claims in a wide variety of settings. In McLean Associates, Inc. v. Wm. M. Mercer-Meidinger-Hansen,[128] for instance, the creator of computer software brought a copyright infringement action against the corporation that had formerly employed him. The court held that the evidence supported the finding that a non-exclusive license could be construed from the circumstances.[129] Another court found a right to reproduce and sell sound recordings of musical competitions where no written agreement existed based on the theory of implied license.[130] In another case, a book author was held to have granted a non-exclusive license for another author to use portions of the book when he allowed the other author a chance to review and revise the manuscript.[131]
{45} Authors of a vast majority of World Wide Web materials intend their material to be publicly accessible. While there is no doubt that most of that material is, by default, subject to copyright protection, it is almost certainly the case that a non-exclusive implied license protects individuals engaged in basic Web browsing activities that would otherwise be considered infringing. For instance, in order to view a document on the Web at all, a copy must be transmitted to the viewer's computer, placed in memory, interpreted by browsing software, and displayed on the viewing party's video display. Taken out of context, this process, in and of itself, seems to involve a series of acts that might infringe.[132] But these activities are central to the functionality of the Web in the first place. Finding that they are infringements would create an infringement when users browsed materials in a way the owner specifically intended, a seemingly absurd result.[133]
{46} An analogous situation exists with computer programs that must be "copied" into a computer's memory in order to be executed. Federal courts, when faced with these situations, have held that this process involves a duplication for purposes of the copyright statute."[134] However, recognizing that this posed problems for the very functionality of computer software, and would make it illegal to use the software in the first place, Congress enacted a specific provision of the copyright statute to allow individuals to copy computer programs where the copy is created "as an essential step in the utilization of the computer program in conjunction with a machine and that it is used in no other manner."[135] That provision goes on to authorize the creation of archival or back-up copies.
{47} With this rationale in mind, one commentator has argued that copying Web pages falls under the Section 117 protection.[136] Recognizing that a strict reading of the copyright statute means that copying, distribution and display occur when in the process of browsing the World Wide Web, he notes that the [World Wide Web page] is then transmitted through the computer network and 'fixed' in a RAM of the user's computer. The work has now been reproduced, implicating the Section 106(1) right of the copyright holder if the user then saves the transfer work onto his hard disk, assuming the transfer of the work was an authorized one, the copy on the hard disk is an archival copy authorized by Section 117.[137]
{48} The only caveat to this is that if the reproduction is a work that is already an infringing copy, or if the reproduction by transmission would be in excess of the rights allowed by the copyright holder, then any copies made would be infringing ones.[138] If one assumes, however, that no owner puts material on the Web which is not intended to be transmitted to users all over the world, the initial transfer is not in excess of the rights allowed by the owner.[139]
{49} It is not clear that the language of Section 117 supports this reasoning. Even if Section 117's unique protection for computer software does not apply to Web material, it lends support, by analogy, to the idea that implied non-exclusive licenses exist which authorize the duplication, distribution and display of that material. Section 117 is, in some respects, nothing more than a codification of what would otherwise be an implied non-exclusive license.
{50} The relatively few commentators who have analyzed the applicability of the implied license doctrine to on-line materials have recognized that it must have wide reaching consequences.[140] One commentator concludes that much of the material distributed over the Internet is made available for free, and that accessing, and even storing it can come within the scope of creator's implicit or explicit license to the reader.[141] Others contend that the doctrine of implied consent as applied to on-line materials would "appropriately allow the transmission and copying necessary to facilitate their use within the electronic realm."[142] Of course, there are important questions remaining on the exact scope of the implied license that might be involved here, and the analysis is a fact intensive one. Still, the implied license doctrine will undoubtedly legitimize most end-user activities browsing activities in such a way as to shield the linking party from a contributory infringement claim.
{51} Not every use of a copyrighted work is a violation of the law. The statutory notion of fair use was developed to cover situations where reproducing or using an owner's work is not harmful to the owner, and the ability to do so is an important part of public discourse.[143] The fair use doctrine acts as a shield against copyright liability in these instances.
{52} There are four basic statutory elements to a fair use defense: (1) the purpose and character of the use (including whether the use is commercial or non-commercial in nature); (2) the nature of the copyrighted (original) work; (3) the amount or proportion that was taken or copied; and (4) the economic impact of the use on the copyright owner of the original work.[144]
{53} Fair use analysis turns on an examination of the equities involved in the defendant's use, making the analysis "so flexible as virtually to defy definition."[145] Nonetheless, courts have repeatedly applied the four factors to invalidate infringement claims where the defendant's actions would otherwise constitute infringement, and the statute itself was intended to memorialize the judicial doctrine that had been developing in the common law at the time of its inception.[146]
{54} One might argue that many WWW activities that would otherwise constitute an infringement may be protected as fair uses under Section 107. This is due to the nature of the Web, where, "if the document is made freely available for copying in the first place, it is not necessary to inquire whether private copying was a fair use: fair use excuses prima facie infringements, and where the copying was permitted, there is not even prima facie infringement."[147]
{55} In Sony Corp. v. Universal City Studios[148], the United States Supreme Court recognized that, with the new electronic media copyright, owners sometimes find nothing objectionable about what would otherwise be viewed as violations or infringements of their rights, thus, supporting a finding that such activities constitute fair use.[149] In Sony, the court reviewed the status of programs designed to be broadcast on television and noted that many important producers of national and local television programs find nothing objectionable about the enlargement of the size of the television audience which results from the practice of time-shifting for private home use.[150] The court went on to point out that "the user of the copyrighted work is not required to pay a fee for access to the underlying work."[151] The court seemed to recognize that the traditional method by which copyright owners capitalize upon advertiser sponsored free public broadcast over the public airwaves is predicated upon the assumption that compensation for the value of displaying the works will be received in the form of advertising revenues.[152] The court concluded that because the public had been "invited to witness [the programs in their] entirety free of charge," copying them for time-shifting purposes was a "fair use" of the copyrighted work.[153]
{56} Similarly, most of the World Wide Web is freely accessible to the public. Owners of materials placed on the Web presumably want users to view them, and it seems likely that browsing activities, might be deemed non-infringing as fair use.[154] As one court has already observed, "absent a commercial or profit-depriving use, digital browsing is probably a fair-use."[155] In fact, there are strong policy arguments to support such a conclusion.[156] Thus, in the linking scenarios at issue here, it seems reasonable to conclude that, usually, the end-user's browsing activities seem to constitute fair use, even if they are browsing "through" an unauthorized link.
{57} However, unlike the copy made during simple browsing, that is "only necessary because humans cannot otherwise perceive digital information,"[157] the act of unauthorized linking itself might implicate more blatant commercial interests. This makes a fair use defense much less likely to be successful in some linking scenarios, since of the four fair use factors, the effect of the use upon the potential market is the most important.[158] This is important because an unauthorized link might not conform with the intended revenue generation scheme that the author of the original work had in mind.[159] For instance, one could imagine the publisher of a WWW-based newspaper placing advertising material on the "front page" but not on the subsequent articles. This is a viable revenue generator only if the users peruse the pages in order (they at least need to see the first page to see the ads). An unauthorized link directly to a subsequent article, however, would display the content without the user having been exposed to the front page's advertisements. The situation is worse if you imagine that the potential advertiser has the option of placing an ad with not only the newspaper, but also with a service like TotalNEWS, that envelopes the content of others in its own advertisements, a blatantly competitive commercial use. Where this type of economic effect on the ability of the author to make a profit off of his copyrighted work is apparent, it seems hard to imagine a court deeming the unauthorized linking itself a fair use.[160]
{58} Since, as noted above, the end user's activities are presumably less commercially motivated, the fair use defense is much more applicable when assessing whether or not the end user's browsing infringes. As such, while the linking party itself might not be able to defend its actions on fair use grounds, if the direct infringement assertion against the end user fails because of the fair use defense, then the contributory infringement claim against the linking party must fail as well.
{59} There are other intellectual property doctrines that may prove relevant to unauthorized linking scenarios and give rise to a civil cause of action.[161] A plaintiff might assert claims under the Lanham Act for trademark infringement,[162] dilution,[163] or false designation.[164] Barring preemption, a plaintiff might also turn to a cause of action based on state common law theories including misappropriation, unfair competition, and contract.[165]
Trademark Infringement
{60} Section 32(1) of the Lanham Act allows a plaintiff to recover for trademark infringement if he can prove that the defendant used a "reproduction, counterfeit, copy, or colorable imitation of a registered mark in connection with the sale, offering for sale, distribution, or advertising of any goods or services" without consent of the mark's owner, and which causes or is likely to cause confusion.[166]
{61} Generally, courts require the plaintiff to prove only that he owns the prior rights in the mark and that the defendant's use of the mark is likely to cause consumer confusion, deception, or mistake.[167] In determining whether the use is likely to cause consumer confusion, the courts will generally weigh seven factors: (1) the degree of similarity between the marks in appearance and suggestion; (2) the similarity of products or services for which the name is used; (3) the area and manner of concurrent use; (4) the degree of care likely to be exercised by consumers; (5) the strength of the complainant's mark; (6) actual confusion; and (7) an intent on the part of the alleged infringer to palm off his products as those of another.[168]
{62} An unauthorized linking scenario seems likely to involve potential trademark liability if the linking party's site incorporates marks belonging to the party to whom he is linking. The link alone is probably not enough. However, where the link in question is of the invoke-to-load type, it is not uncommon for the link to be designated by an icon or "clickable" text that informs the user about what can be found when the link is actually invoked. If the icon is a copy or colorable imitation of a trademark, it is possible that a user could be confused as to whether the linking party is associated with the complainant. An auto-load link alone might not implicate trademark directly, since the linking party does not need to use a copy or colorable imitation, but rather only provides a URL enabling the end user to manipulate the plaintiff's mark. If the linking party uses the plaintiff's mark in some independent manner, liability may attach as it would in other contexts.
{63} Section 33(b)(4) of the Lanham Act sets out a defense to a trademark infringement action for "use, otherwise than as a mark, of the party's individual name in his own business, or of the individual name of anyone in privity with such party, or of a term or device which is descriptive of and used fairly and in good faith only to describe the goods or services of such party, or their geographic origin…."[169] This defense represents the principle that parties should not be able to appropriate descriptive language by way of trademark registration.[170] Courts have generally required a three-part showing to establish this defense, viz., (1) good faith, (2) non-trademark use, (3) of a term accurately describing the defendant's goods or services.[171]
{64} In order to establish the defense, the defendant must show that his use of the mark is descriptive.[172] To determine the character of the use, courts measure the use against the idea that "if the mark imparts information directly it is descriptive[;] if it stands for an idea which requires some operation of the imagination to connect it with the goods, it is suggestive."[173] It is not, however, a requirement that a descriptive term depict the product itself, but only that the term refer to a characteristic of the product.[174] "[T]he true test [of descriptiveness] is one of consumer perception--how is [the term] perceived by the average prospective consumer?" [175]
{65} Finally, the Ninth Circuit has created the "nominative fair use defense."[176] Judge Kozinski, writing for the court, stated that where the defendant uses a trademark to describe the plaintiff's product, rather than its own, we hold that a commercial user is entitled to a nominative fair use defense provided he meets the following three requirements: First, the product or service in question must be one not readily identifiable without use of the trademark; second, only so much of the mark or marks may be used as is reasonably necessary to identify the product or service; and third, the user must do nothing that would, in conjunction with the mark, suggest sponsorship or endorsement by the trademark holder.[177]
Dilution
{66} The Federal Trademark Dilution Act of 1995 ("Dilution Act") created a new federal cause of action in Section 43(c). The law, effective as of January 16, 1996, entitles an "owner of a famous mark" to injunctive relief against another's commercial use of the mark if the "use begins after the mark has become famous and causes dilution of the distinctive quality of the mark."[178] In order to prevail on its dilution claim under federal law, a plaintiff must demonstrate (1) ownership of a distinctive trade dress or famous mark, and (2) actual dilution.[179] The statute also requires the defendant's use to be "commercial" and "in commerce," reflecting "the fact that the bill, like the Lanham Act itself, requires some aspect of interstate commerce to be present before the dilution provision can be triggered."[180]
{67} The Dilution Act defines dilution to mean "the lessening of the capacity of a famous mark to identify and distinguish goods or services, regardless of the presence or absence of (1) competition between the owner of the famous mark and the other parties, or (2) likelihood of confusion, mistake, or deception."[181] While definite standards for analyzing dilution under Section 43(c) have not yet emerged, the statute "protect[s] famous trademarks from subsequent uses that blur the distinctiveness of the mark or tarnish or disparage it."[182] This language mirrors traditional state dilution analysis, under which dilution can generally be founded through establishing blurring or tarnishment.[183] Tarnishment is generally said to occur when the plaintiff's famous mark will suffer negative associations through a defendant's use of the mark in connection with shoddy goods or unseemly, lewd, or obscene activities.[184] Blurring occurs where "the defendant uses or modifies the plaintiff's trademark to identify the defendant's goods and services, raising the possibility that the mark will lose its ability to serve as a unique identifier of the plaintiff's product."[185]
{68} As with trademark infringement, the key to assessing a linking party's liability lies in determining whether the act of providing the link, in and of itself, constitutes the requisite "use" under the statute. Recognizing that trademark law and the Dilution Act seek to protect the same subject matter (marks) from differing harms (doing business on another's reputation and dilution of the mark, respectively), it would appear that "use" is the same under both theories. It therefore appears that, in the case of unauthorized linking, creating a link that incorporates a famous mark, the use of which is commercial, in commerce, and causes dilution, would be proscribed by the Dilution Act.
{69} Under this analysis, the creator of the Dilbert Hack Page would likely escape liability, for, while the Dilbert mark is certainly famous and this use will likely cause blurring dilution, the use is neither commercial, nor in commerce. TotalNEWS, however, seems likely to incur liability under such a claim. At least some, if not all, of the marks used by TotalNEWS on its page, as first presented to the viewer, are famous. Moreover, the commercial use in commerce elements appear to be met by virtue of the advertising revenue generated by the page. Finally, the use of the famous marks will almost certainly cause dilution as defined by the statute.[186] If, however, TotalNEWS were to avoid actually incorporating the marks into its own HTML, instead, using generic references to the linked sites that do not actually "use" the mark, then there might not be the requisite use, thereby escaping liability.
False Designation
{70} The Lanham Act also creates a statutory tort allowing recovery for false designations of origin and false representations in Section 43(a).[187] In general, a defendant is liable for false designations of origin and false descriptions if his conduct is likely to cause confusion,[188] or "in commercial advertising or promotion, misrepresents the nature, characteristics, qualities, or geographic origin of her or another person's goods, services, or commercial activities."[189] The plain language of the statute indicates that likelihood of confusion is not a required element for a claim to false designation under the statute's "false or misleading" language. On the other hand, if likelihood of confusion is shown, the statute does not require the plaintiff to prove the falsity of the defendant's representation. In practice, a false representation claim arises when a trademark or name or distinguishing characteristics of a product or service is used in a false or deceptive manner, either to the misrepresented fact or to the association between the advertiser and mark owner.[190] The statute is broadly construed[191] and covers both registered and unregistered marks.[192]
{71} Unlike trademark infringement and dilution, the false designation provision of the Lanham Act may have the flexibility to encompass unauthorized linking activities like those described here. Where an unauthorized link involves framing, for instance, it seems very possible that, absent clear disclaimers, confusion might occur. As one court noted when looking at a situation where one website framed another, "in short, a visitor to [the linking] site could easily have the impression that they were actually at [the other] site."[193]
Misappropriation
{72} Misappropriation is a type of unfair competition recognized by the United States Supreme Court in which the plaintiff complains of unauthorized appropriation by a competing defendant of property in which the plaintiff has invested substantial time, skill, and money.[194] While early cases held that federal law preempts state common laws providing protection for facts,[195] some modern courts have held that Section 301 of the 1976 Copyright Act does not preempt state law protection of facts.[196]
{73} Before its decision in Erie R.R. Co. v. Tompkins,[197] the United States Supreme Court held in International News Service v. Associated Press[198] that under general federal common law, misappropriation of "hot news" was unfair competition and, hence, actionable.[199] There, the defendant, I.N.S., was pirating news stories originally published by A.P.[200] The Court upheld an order barring the defendant from such action, noting that "[the news developed by AP at significant expense] has all the attributes of property necessary for determining that a misappropriation of it by a competitor is unfair competition because contrary to good conscience."[201]
{74} While Erie may cast some doubt on the continued viability of I.N.S. in federal law, the misappropriation type of unfair competition claim lives on in state courts.[202] Indeed, as the recent Second Circuit decision in National Basketball Association v. Motorola[203] indicates, misappropriation as a cause of action still survives in some form. In that action, the National Basketball Association sued Motorola for unauthorized use (in this case rebroadcast) of professional basketball game scores during the course of the game.[204] The court held that a "hot news" misappropriation claim lies only where the following elements are present: (1) the plaintiff generates or collects information at some cost or expense, (2) the value of the information is highly time-sensitive, (3) the defendant's use of the information constitutes free-riding on the plaintiff's costly efforts to generate or collect it, (4) the defendant's use of the information is in direct competition with a product or service offered by the plaintiff, and (5) the ability of other parties to free-ride on the efforts of the plaintiff would so reduce the incentive to produce the product or service that its existence or quality would be substantially threatened.[205]
{75} Interestingly, even the whittled-down misappropriation claim recognized by the Second Circuit may face constitutional preemption. First, such state protection of facts and ideas may so offend the federal statutory scheme embodied in the 1976 Act as to require its preemption under the Constitution's Supremacy Clause.[206] Second, as Professor Goldstein notes, "state protection of ideas and facts may in certain cases offend constitutional provisions, specifically the first amendment's guarantee's of free speech and press as incorporated by the fourteenth amendment."[207] This latter theory of preemption would seem to make sense here, as the first element set out by the Second Circuit requires that the plaintiff have collected or generated information at some cost to himself. "Information" would seem to indicate first amendment protected facts or ideas. While one might argue that "information" also encompasses the expression of ideas, the second element's requirement that the information be "highly time-sensitive," seems to support the notion that "information," as used by the court, includes only facts or ideas, as it is difficult to imagine how expression would be "highly time-sensitive." The copyright statue was crafted to exclude protection for such "information," and it seems plausible that any scheme that works as an end-around to the copyright statute is subject to critical review under preemption doctrines.[208]
{76} Notwithstanding preemption problems, though, the surviving state law misappropriation theory may provide relief in some cases of unauthorized linking. In fact patterns like the Dilbert Hack page, however, the fact that United Feature Syndicate (UM) and Mr. Wallach were not in competition precludes recovery by UM under a misappropriation claim. The TotalNEWS scenario seems a more likely candidate for misappropriation. The plaintiffs there could likely show that they collect and generate highly time-sensitive information (news). TotalNEWS' use of this information to generate advertising revenues seems to constitute "free-riding" on the plaintiffs' efforts. Moreover, TotalNEWS' use of this information to generate advertising revenue appears to be in direct competition with the plaintiffs' generation of such revenue, even though the two are not in direct competition in the news gathering field. Finally, the case could be made that TotalNEWS' free-riding would act as a disincentive against the continued existence of the plaintiffs' news gathering services or, at a minimum, their quality would be substantially threatened. Presumably, the loss of advertising revenue to a TotalNEWS-like competitor would at least have an adverse affect on the quality of the plaintiffs' news gathering efforts. TotalNEWS could be said to be "endeavoring to reap where it has not sown . . . in order to divert a material portion of the profit from those who have earned it to the those who have not . . ."[209]
Passing (Palming) Off
{77} As noted above, state common law unfair competition claims generally track the requirements for recovery under Lanham Act § 43(a).[210] The two elements which must generally be established in order to sustain a cause of action for passing off are: (1) plaintiff's use of its trade name has acquired a secondary meaning; and (2) the similarity of the name used by the defendant's place of business would be likely to confuse the public.[211] Since, generally, ''the same facts which would support an action for trademark infringement would also support an action for unfair competition,"[212] much of the analysis in the trademark infringement discussion above would apply here as well.
Contract
{78} Since federal copyright law denies protection for ideas, some plaintiffs will be forced to turn to state law for relief. By contract, parties can protect both those subject matters within and without the realm of the Copyright Act. According to the Seventh Circuit, at least, some contracts to protect intellectual property avoid preemption and are viable.[213] There, the court upheld the viability of "shrinkwrap" licenses governing commercial software products.[214] By analogy, a license on a web page that plainly, and within the dictates of contract law, provide for viewing of the web product only upon acceptance of the terms of the license might be argued to create a valid and enforceable contract between the parties that allows certain uses of the copyrighted material at issue to be deemed a breach of contract.[215]
{79} Given that the end-user, not the linking party is manipulating the material, such terms would govern the user's actions, not the linking party's. If those terms prohibit the end user from viewing or loading the materials via unauthorized links, then, arguably, the implied license to engage in normal browsing activities is limited in such a way as to make the direct linker a direct infringer in some cases. If that occurs, then the linking party becomes subject to a claim of contributory infringement of both the participatory and means-to-infringe varieties based on the users' underlying infringement.
{80} As Ethan Katsh points out in his insightful book, Law in a Digital World,[216] "The new [digital hypertext] environment, in which there are new links, new opportunities to communication and new tools for creating, is one that encourages changes in how we look upon created works and in how we describe and think about them."[217] Perhaps, as some have suggested, the focus should not be on copyright and established intellectual property at all, but rather on the nature of the use and the author's ability to control it.[218] There are, for instance, technologies that a site owner can employ to block unauthorized linking without turning to legal recourse.[219] We might rely upon more sophisticated technologies that effectively protect the author's interests in copyrighted material by more precisely tracking, and accounting for the public's use of the material. In a world where traditional legal doctrines break down, there is at least some temptation to turn to this sort of self-regulation as a means of maintaining order.[220] This temptation, however, may ultimately prove to be shortsighted, as such private ordering schemes might have unintended consequences that threaten fundamental freedoms.[221] Whether it is through a restructuring of current intellectual property law principles, or some more imaginative solution, it seems hard to imagine that an activity as fundamental as linking will be left clouded in legal uncertainty for too long. But, as seen here, the current intellectual property framework strains, at best, to provide the analytical tools necessary to address the issue.
[**]NOTE: All endnote citations in this article follow the conventions appropriate to the edition of THE BLUEBOOK: A UNIFORM SYSTEM OF CITATION that was in effect at the time of publication. When citing to this article, please use the format required by the Seventeenth Edition of THE BLUEBOOK, provided below for your convenience.
Edward A. Cavazos and Coe F. Miles, Ph.D., Copyright on the WWW: Linking and Liability, 4 RICH. J.L. & TECH. 3, (Winter 1997), at http://www.richmond.edu/~jolt/v4i2/cavazos.html.
[1] Copyright © 1997 Edward A. Cavazos <ecavazos@interliant.com> and Coe F. Miles <cmiles@ipnotes.com>. Mr. Cavazos is Senior Vice President, General Counsel of Interliant, Inc. and an Adjunct Professor of Network Law at the University of Houston Law Center. Dr. Miles is an associate attorney at Fish & Richardson in Houston and holds a Ph.D. in computer engineering. Invaluable research and writing assistance was provided by Tim Langenkamp <tcl@pobox.com>, a third year law student at the University of Houston Law Center. This paper was first presented at the Buffalo Law Review's "Cyberlaw" conference in March, 1997.
[2] For a wonderful history of the Internet and its predecessor technologies, see KATIE HAFNER & MATTHEW LYONS, WHERE WIZARDS STAY UP LATE (1996); see also Barry M Leiner et al., A Brief History of the Internet (visited Feb. 26, 1998) <http://www.isoc.org/internet-history/brief.html> (this text is revised periodically by the author).
[3] ACLU v. Reno, 929 F. Supp. 824, 836 (E.D. Pa. 1996) ("fast becoming the most well-known on the Internet, is the'World Wide Web'") , aff'd, 117 S.Ct 2329 (1997); see also Internet Resource Discovery Services on NSFNET by Packets (log, ASCII) (visited Mar. 3, 1998) <http://www3.mids.org/growth/internet/> (comparing the growth in WWW-related traffic with non-WWW applications such as FTP and gopher).
[4] A "killer app" is a "use of technology so attractive to consumers that it fuels market forces and makes an invention all but indispensable . . . ." BILL GATES, THE ROAD AHEAD 68 (1995). Other examples of killer apps include the electric light (electricity) and word processing software (the microcomputer). See id. at 68-69.
[5] The HyperText Markup Language (HTML) is a markup language used to create hypertext documents that are portable from one computer platform to another. The HTML standard is developed and promulgated by the World Wide Web Consortium (W3C). See World Wide Web Consortium Home Page (visited Feb. 28, 1998) <http://www.w3.org/pub/WWW/>. See also HTML: Working and Background Materials (general introduction and overview of the HTML) (last modified Feb. 27, 1998) <http://www.w3.org/pub/WWW/MarkUp/>; HTML 2.0 Materials (current adopted version of the HTML specification) (last modified Dec. 21, 1995) <http://www.w3.org/pub/WWW/MarkUp/html-spec/>; HTML 3.2 Reference Specification (proposed specification for the next version of HTML) (visited Feb. 28, 1998) <http://www.w3.org/pub/WWW/TR/PR-html32-961105.html>.
[6] Popular web browsers include Netscape Navigator, NCSA Mosaic, Lynx, and Microsoft Internet Explorer.
[7] Here, "interpret" is used in its technical sense. A program, such as a browser, designed to process an HTML document does so by (1) sequentially stepping through the document's text and, when an HTML instruction is found, (2) translating that instruction into one or more instructions which are directly executable by the computer, and then (3) executing those instructions. This process is repeated as each HTML instruction is encountered by the browser. In contrast, a compiler translates all the instructions in a computer program file into a series of lower level instructions (directly executable by the target computer), before any single instruction is executed. Some other interpretive computer languages are BASIC, SNOBOL, and ALGOL. Common compiled languages include C, FORTRAN, and PASCAL. See CARLO GHEZZI & MEHDI JAZAYERI, PROGRAMMING LANGUAGE CONCEPTS 34-35 (1982).
[8] United Feature Syndicate, Inc., The Dilbert Zone (visited Feb. 24, 1998) <http://www.unitedmedia.com/comics/dilbert/>.
[9] Daniel Wallach, See David Wallach's Home Page (visited Feb. 24, 1998) <http://www.cs.princeton.edu/~dwallach/>.
[10] While the Dilbert Hack Page (DHP) has been disabled, Mr. Wallach maintains a fascinating archive that Chronicles his efforts and the responses they received. Daniel Wallach, Dilbert Hack Page Archives (last modified Sep. 28, 1997) <http://www.cs.princeton.edu/~dwallach/dilbert/>. The archive includes copies of all correspondence received and sent to United Feature Syndicate, Inc. regarding the DHP as well as technical descriptions of how the DHP worked.
[11] Daniel Wallach, United Media's First Letter (dated July 19, 1996) (last modified Aug. 4, 1996) <http://www.cs.princeton.edu/~dwallach/dilbert/letter1.html>.
[12] Daniel Wallach, United Media's Second Letter (dated July 26, 1996) (last modified Aug. 4, 1996) <http://www.cs.princeton.edu/~dwallach/dilbert/letter2.html>.
[13] Daniel Wallach, The Dilbert Hack Page is Gone (dated August 4, 1996) (last modified Aug. 4, 1996) <http://www.cs.princeton.edu/~dwallach/dilbert/page-gone.html>.
[14] TotalNEWS Website, Home Page (visited Feb. 28, 1998) <http://www.totalnews.com/>. See also Noah Robischon, The Netly News - The Bad News About TotalNEWS (December 5, 1996) <http://cgi.pathfinder.com/netly/article/0,2334,11543,00.html>.
[15] Frames allow a web page designer to partition a user's browser window into two or more individually named regions. This, in turn, allows the designer to display information in any of the specified regions independently of the other regions. While frame capability may become part of the HTML standard in the future, only Netscape 2.0 and higher and Microsoft's Internet Explorer are currently known to support frames. For an introduction to frames, see LAURA LEMAY, TEACH YOURSELF WEB PUBLISHING WITH HTML 3.2 IN A WEEK 409 (3d ed. 1996). See also Digital Equip. Corp. v. AltaVista., Inc., 960 F. Supp. 456, 461 n.12 (D. Mass. 1997) (explaining WWW framing).
[16] Advertisers (including AT&T Corporation and MasterCard International) reportedly pay $35 per thousand exposures on the TotalNEWS site. Debra Aho Williamson, New Technology Tests Limit of Online Copyright, Advertising Age (electronic magazine) (visited Feb. 28, 1998) <http://adage.com/interactive/articles/19961125/article4.html>.
[17] Media Groups File Suit Against TotalNEWS On Web Site Framing, THE WALL STREET JOURNAL, Monday, February 24, 1997 at B8. See also Frame Technology: the Internet Equivalent of Pirating?, Law Journal Extra, (electronic magazine) (visited Feb. 28, 1998) <http://www.ljx.com/internet/complain.html>.
It should be noted that TotalNEWS explicitly disclaims the information displayed when a user selects any of the services linked to by TotalNEWS. See the "terms of service" link on TotalNEWS' home page, <http://www.totalnews.com/>. See also Debra Aho Williamson, New Technology Tests Limits of Online Copyright, ADVERTISING AGE (electronic magazine) (visited Feb. 28, 1998) <http://adage.com/interactive/articles/19961125/article4.html>.
[18] Stipulation and Order of Settlement and Dismissal, Southern District of New York, 97 Civ. 1190, June 9, 1997. See also the Law Journal Extra website, <http://www.ljx.com/internet/totalse.html>.
[19] Id. at ¶ 3.
[20] Id. at ¶ 4.
[21] See discussion infra Section V, End Users Defenses.
[22] 17 U.S.C.A. §§ 101-1010 (West 1996). For an on-line version of Title 17 see The Legal Information Institute Cornell Law School, Title 17 WWW Page <http://www.law.cornell.edu/uscode/17/>.
[23] 17 U.S.C.A. § 102(a) (West 1996).
[24] Feist Publications, Inc. v. Rural Tel. Serv. Co., Inc., 499 U.S. 340, 345 (1991).
[25] 17 U.S.C.A. § 101 (West 1996).
[26] Although all works that can be protected must be original works of authorship fixed in a tangible medium, not all such works are protectable. For instance, copyright protection does not "extend to any idea, procedure, process, system, method of operation, concept, principle, or discovery." 17 U.S.C.A. § 102(b) (West 1996).
[27] 17 U.S.C.A. § 106 (West 1996) as amended by Pub L. No. 104-39, § 2, 109 Stat. 336.
[28] Reproductions, or "'copies' . . . are material objects, other than phonorecords, in which a work is fixed by any method now known or later developed, and from which the work can be perceived, reproduced, or otherwise communicated, either directly or with the aid of a machine or device." 17 U.S.C.A. § 101 (West 1996).
[29] A "derivative work" is one "based upon one or more preexisting works, such as a translation, musical arrangement, dramatization, fictionalization, motion picture version, sound recording, art reproduction, abridgment, condensation, or any other form in which a work may be recast, transformed, or adapted." Id. at § 101.
[30] With respect to literary, musical, dramatic, and choreographic works, pantomimes, and motion pictures and other audiovisual works, public display or performance means "(1) to perform or display it at a place open to the public or at any place where a substantial number of persons outside of a normal circle of a family and its social acquaintances is gathered; or (2) to transmit or otherwise communicate a performance or display of the work to a place specified by clause (1) or to the public, by means of any device or process, whether the members of the public capable of receiving the performance or display receive it in the same place or in separate places and at the same time or at different times." 17 U.S.C.A. § 101 (West 1996). (defining what constitutes performing or displaying a work "publicly").
[31] A digital transmission is "a transmission in whole or in part in a digital or other non-analog format." Id. at § 101 (West 1996 & Supp. 1997). The Act also protects a visual artist's rights of attribution and integrity, see 17 U.S.C.A. § 106A (West 1996), semiconductor chip products, see id. at §§ 901-914, and digital audio recording devices and media, see id. at §§ 1001-1010. The Act also protects a visual artist's rights of attribution and integrity (17 U.S.C.A. § 106A (West 1996)), semiconductor chip products (17 U.S.C.A. §§ 901-914 (West 1996)), and digital audio recording devices and media (17 U.S.C.A. §§ 1001-1010 (West 1996)).
[32] The owner of a copyright under the Act has the exclusive rights to do and to authorize any of the aforementioned exclusive rights. 17 U.S.C.A. § 102(a) (West 1996).
[33] Salinger v. Random House, Inc., 811 F.2d 90 (2d Cir.), cert. denied 484 U.S. 890 (1987).
[34] All of the enumerated rights are limited by the Act's "fair use" doctrine set forth in section 107. In addition, the right of reproduction is limited by §§ 108 (reproduction by libraries), 112 (ephemeral recordings), 113 (pictorial, graphic, and sculptural works), 114 (sound recordings), 115 (compulsory license for phonorecords), and 117 (computer programs); the right of public distribution is limited by §§ 109 (effect of transfer of a copy), and 602 (importation of copies); the right of public performance and distribution is limited by §§ 109 (effect of transfer of a copy), 110 (exemption of certain performances and displays), 111 (secondary transmissions), 116 (negotiated licenses), 118 (noncommercial broadcasting), and 119 (private home viewing); the right of public display is limited by §109 (effect of transfer of a copy); and the right in digital transmissions is limited by §114 (sound recordings).
[35] Feist Publications, Inc. v. Rural Tel. Serv. Co., Inc., 499 U.S. 340 (1991).
[36] Id.
[37] See Wavelength Film Co. v Columbia Pictures Indus., Inc., 631 F.Supp. 305 (N.D. Ill. 1986) (because defendant's film is similar only in scenes of faire, summary judgment is granted in favor of defendant); Atari, Inc., v. North American Philips Consumer Elec. Corp., 672 F.2d 607 (7th Cir. 1982) (content that is only capable of expression in more or less stereotyped form will preclude a finding of actionable similarity).
[38] E.g., Alberto-Culver Co. v. Andrea Dumon, Inc., 466 F.2d 705 (7th Cir. 1972) (short phrases do not contain enough creative expression to be copyrightable works of authorship); Harper House, Inc. v. Thomas Nelson, Inc., 889 F.2d 197 (9th Cir. 1989) ("copyright protection does not extend to common property such as standard calendars and area code maps").
[39] 17 U.S.C.A. § 501(a) (West 1996).
[40] Feist, 499 U.S. at 361 (citing Harper & Row, Publishers, Inc. v. Nation Enters., 471 U.S. 539, 548 (1985)).
[41] See Buck v. Jewell, 283 U.S. 191, 198 (1931); Playboy Enter., Inc. v. Frena, 839 F.Supp. 1552, 1559 (M.D. Fla. 1993).
[42] Sega Enterprises v. MAPHIA, 948 F.Supp. 923, 932 (1996); Religious Technology v. Netcom On-Line Communications, Inc., 907 F.Supp. 1361, 1366-67 (N.D. Cal. 1995); Playboy, 839 F.Supp. at 1556.
[43] See Mark A. Lemley, Dealing With Overlapping Copyrights on the Internet, 22 U. DAYTON L. REV. 547 (1997).
[44] See David R. Johnson and David Post, Law and Borders - the Rise of Law in Cyberspace, 48 Stanford L. Rev. 1367, 1385 n.49 (1996) (explaining how WWW browsing necessarily involves making a number of "copies").
[45] See MAI Systems v. Peak Computer, Inc., 991 F.2d 511, 529 (9th Cir. 1993). cert. dismissed, 501 U.S. 1033 (1994). For a critical analysis of the MAI holding, see Niva Elkin-Koren, Copyright Law and Social Dialogue on the Information Superhighway: The Case Against Copyright Liability of Bulletin Board Operators, 13 CARDOZO ARTS & ENT. L.J. 346, 353-55 (1993).
[46] Sega, 948 F.Supp. at 931-932.
[47] See Playboy Enter., Inc. v. Frena, 839 F.Supp. 1552, 1556-57 (M.D. Fla. 1993) (digital file download constitutes display).
[48] See id. at 1556 (finding that downloading of files from a bulletin board system was a distribution under the Act).
[49] "A derivative work is a work based upon one or more preexisting works . . . or any other form in which a work may be recast, transformed, or adapted." 17 U.S.C.A. § 101 (West 1996).
[50] Mirage Editions, Inc. v. Albuquerque A.R.T. Co., 856 F.2d 1341 (9th Cir. 1988), cert. denied, 489 U.S. 1018 (1989).
[51] The "first sale" doctrine holds that the owner of a particular copy lawfully obtained is entitled, without the authority of the copyright owner, to sell or otherwise dispose of the possession of that copy. 17 U.S.C.A. § 109 (West 1996). The Mirage court dismissed appellant's first sale defense by stating that "the right to transfer applies only to the particular copy of the book which appellant purchased and nothing else." Mirage, 856 F.2d at 1344. Apparently, the court considered the "thing" purchased was the book of artprints, and not the individual artprints themselves.
[52] 125 F.3d 580 (7th Cir. 1997).
[53] Id. at 582.
[54] Id.
[55] Id.
[56] Pub. L. No. 101-650, 104 Stat. 5089, 5123-33, codified as amended in 17 U.S.C.A. § 106(a)(3)(A) (West 1996). See section 106A(a)(3).
[57] 17 U.S.C.A. § 101 (West 1996). Under the umbrella of the Lanham Act's "false designation of origin" provision (15 U.S.C.A. § 1125), recent cases suggest federal courts are beginning to acknowledge a right of attribution where the failure to attribute has a commercial effect. See Mark A. Lemley, Rights of Attribution and Integrity in Online Communications, 1995 J. ONLINE L. art. 2, par. 14. While interesting, the effect of federal trademark and unfair competition law is beyond the scope of this paper.
[58] See Columbia Pictures Indus., Inc. v. Aveco, Inc., 800 F.2d 59 (3d Cir. 1986) (holding defendants liable for direct copyright infringement for authorizing a third party to violate one of the five (now six) enumerated rights in section 106. The defendants were the owners of video rental stores which rented out both video cassettes and viewing booths. The court held that the customers' in-store viewing constituted a public performance and that the defendants had illicitly authorized this performance in violation of plaintiff's rights under section 106); ITSI T.V. v. California Auth. Of Racing Fairs, 785 F.Supp. 854, 863 (E.D. Cal. 1992) ("under the 1976 Act the holder of a copyright enjoys the right 'to do' or 'to authorize' certain acts; violation of either of these rights is a 'direct' act of infringement"), rev'd on other grounds, ITSI T.V. Prods., Inc. v. Agricultural Assoc., 3 F.3d 1289 (9th Cir. 1993).
[59] H.R. Rep. No. 94-1476, at 61 (1976), reprinted in 1976 U.S.C.C.A.N. 5659, 5674.
[60] Subafilms, Ltd. V. MGM-Pathe Communications Co., 24 F.3d 1088, 1092 (9th Cir. 1994) ("the addition of the words 'to authorize' was not meant to create a new form of liability for 'authorization' but was intended to invoke the preexisting doctrine of contributory infringement"); Polygram Int'l Publishing, Inc. v. Nevada/TIG, Inc., 855 F.Supp. 1314, 1334 (D. Mass. 1994) ("a defendant can be held contributorily liable for authorizing another to "); Danjaq, S.A. v. MGM/UA Communications, Co., 773 F.Supp. 194, 200-02 (C.D. Cal. 1991) (concluding that the scope of authorization liability should be confined to the bounds of contributory infringement), aff'd, Danjaq, S.A. v. Pathe Communications Corp., 979 F.2d 772 (9th Cir. 1992).
[61] Kenneth Freeling and Joseph E. Levi, Will Provider Liability Unravel the Web?, 217 N.Y. L.J 13 (1997) (analyzing the related but separate issue of a linking party's liability for linking to a site containing infringing works).
[62] A Uniform Resource Locator (URL) is the world wide web's standard means of specifying a location, or site. URL's are commonly comprised of three parts: (1) protocol part, (2) site or host name part, and (3) the file location part. For example, the fictitious URL "http://wizBang.com/aFile.html" specifies the http protocol (the protocol part), a site called "wizBang.com" (the host name part), and a file called "aFile.html" (the file location part). Other well known protocols include "ftp" (file transfer protocol), "usenet", "mailto", and "Gopher." For further information on the HTTP protocol, see World Wide Web Consortium's Technical Report Page (last modified Feb. 24, 1998) <http://www.w3.org/pub/WW W/Protocols/>.
[63] See Mirage Editions, Inc. v. Albuquerque A.R.T. Co., 856 F.2d 1341 (9th Cir. 1988), cert. denied, 489 U.S. 1018 (1989).
[64] To hold otherwise would extend the moral rights concept beyond the bounds of its appropriate role in U.S. copyright law. See Lee v. Alberquerque A.R.T. Co., 125 F.3d 580 (7th Cir. 1997).
[65] Religious Technology v. Netcom On-Line Communications, Inc., 907 F.Supp. 1361, 1370-71 (N.D. Cal. 1995); Sega Enterprises Ltd. v. MAPHIA, 948 F.Supp. 932 (N.D. Cal. 1996); Marobie-FL, Inc. v. National Association of Fire Equipment Distributors, 983 F. Supp. 1167 (N.D. Ill. Nov. 13, 1997) (declining to find direct infringement where the defendants "did not engage in any of the activities themselves"). Edward A. Cavazos and G. Chin Chao, Computer Bulletin Board System Operator Liability for the Infringement of their Users, 4 TEX. INTELL. Prop. L.J. 13, 17 (1995) (arguing for the application of this rule).
[66] See Playboy Enterprises, Inc. v. Webbworld, Inc., 968 F.Supp. 1171 (N.D. Tex. 1997)(Webbworld I) and Playboy Enterprises, Inc. v. Webbworld, Inc., No. CIV. 3-96-CV-3222-H, 1997 WL 817312 (N.D. Tex. Dec. 11, 1997)(Webbworld II). In the Webworld opinions, the court held the defendants liable as direct infringers based on the behavior of their software, which was programmed to automatically collect images from USENET (public discussion forums on the Internet) and make them available via the defendant's WWW site. Webbworld II, at 2. Included in some of the images processed were copyrighted photographs from Playboy magazine. Id. at 3-4. The reasoning is problematic on a number of grounds. As clearly recognized by the court in Webworld II, the actual "copying' at issue occurred as part of an automated process that resulted in between 5,000 and 10,000 images being transferred from the USENET discussion forums to the Webbworld WWW site. Id. at 3. The defendants did not select the images, nor were they necessarily even aware of the existence of a handful of infringing images processed in this way. The courts mistakenly equated the acts of the automated software employed by the Webbworld defendants as their own acts. Id. at 6. Or, at best, when it recognized the defendants' lack of direct control of the infringing activity, brushes it aside. Webbworld I, 968 F. Supp. 1171, at 1175 ("Even the absence of the ability to exercise such control, however is no defense to liability"), Webbworld II at 6 ("…having developed and launched the [] software for commercial use [they] cannot now evade liability by claiming helplessness in the face of its 'automatic' operation."). In fact, the right approach would include a recognition that the software, though written and initially launched by the defendants, functions here in the role of the direct infringer. Like the defendant in Netcom, the defendants in Webbworld cannot be treated as direct infringers as they did not have the requisite volition to copy that is required of direct infringers. see Cavazos, supra note 65, at 16; Religious Technology v. Netcom On-Line Communications, Inc., 907 F.Supp. 1361, 1372 (N.D. Cal. 1995) (questioning whether "mere possession of a digital copy on a BBS that is accessible to some members of the public constitutes direct infringement). Instead, they should be treated as contributory infringers so that important questions regarding their knowledge of the software's infringing activities can play a role in assessing their liability. Normally, of course, acts that constitute the necessary direct infringement upon which to base a contributory infringement claim are committed by humans. Here, however, this novel problem of the missing direct infringer is surely what leads the courts to conflate the role of direct infringer and contributory infringer and hold the Webbworld defendants liable as direct infringers.
[67] Sega, 948 F.Supp. at 932; Netcom 907 F.Supp. at 1366-67.
[68] While an authoritative opinion directly on point cannot yet be found in the United States, an interesting opinion was issued in October 1996 in Scotland, granting an interim interdict against a defendant newspaper that was linking to the stories of its competitors. What the Judge Said in "The Shetland Times" Case, (visited Feb. 28, 1998) <http://www.shetland-news.co.uk/opinion.html>.
[69] Sony Corp. of America v. Universal City Studios, Inc., 464 U.S. 417, 434 (1984). In contrast, the Patent Act defines anyone who actively induces or contributes to another's infringing activity as an infringer. Id. at 435 (citing 35 U.S.C.A. § 271(b), (c) (West 1996)). Contributory copyright infringement is acknowledged as having been influenced by the Patent Act, Alfred P. Ewert & Irah H. Donner, Will the New Information Superhighway Create "Super" Problems for Software Engineers? Contributory Infringement of Patented or Copyrighted Software-Related Applications, 4 Alb. L.J. SCI. & TECH. 155, 187 (1994) (stating that "[t]he doctrine of contributory copyright infringement appears to have been borrowed …from the contributory patent infringement doctrine").
[70] Sony, 464 U.S. at 435.
[71] Gershwin Publishing Corp. v. Columbia Artists Management, Inc., 443 F.2d 1159, 1162 (2d Cir. 1971).
[72] Lewis Galoob Toys, Inc. v. Nintendo of Am., Inc., 780 F.Supp. 1283, 1298 (N.D. Cal. 1991) ("[a]bsent direct infringement, there is no contributory infringement").
[73] See 3 M. NIMMER AND D. NIMMER, NIMMER ON COPYRIGHTS § 12.04[A][2][L3] (1997).
[74] Sony, 464 U.S. at 434.
[75] Id. at 435.
[76] 464 U.S. 417 (1984).
[77] Id. at 419-20.
[78] Id. at 420.
[79] Id. at 456.
[80] Id. at 423.
[81] Id.
[82] Id. at 442; 17 U.S.C.A. § 107 (West 1996).
[83] Id. at 491-93.
[84] Libraries, while serving as good examples, need not actually worry about this type of liability since they may be exempt from liability for the infringing conduct of those who use the library reproduction equipment unsupervised. See 17 U.S.C.A. § 108(f)(1) (West 1996).
[85] 689 F.Supp. 221 (S.D.N.Y. 1988).
[86] Id. at 228.
[87] Id. at 227-28. The court incorrectly stated that in the intellectual property context vicarious liability and contributory infringement are one and the same. Id. at 228 n.8. The court, however, applied the Sony analysis. Id. at 228.
[88] 847 F.2d 255 (5th Cir. 1988).
[89] Id. at 264.
[90] Id. at 262.
[91] See Gershwin Publishing Corp. v. Columbia Artists Management, Inc., 443 F.2d 1159, 1162 (2d Cir. 1971).
[92] 256 F.Supp. 399 (S.D.N.Y. 1966).
[93] Id. at 401.
[94] Id. at 401-02.
[95] Id.
[96] 443 F.2d 1159 (2d Cir. 1971).
[97] Gershwin, 443 F.2d at 1160-61.
[98] Id. at 1162-63.
[99] Id. at 1163.
[100] Id
[101] 76 F.3d 259 (9th Cir. 1996).
[102] See Fonovisa, Inc. v. Cherry Auction, Inc., 847 F.Supp. 1492 (E.D. Cal. 1994), rev'd, 76 F.3d 259 (9th Cir. 1996).
[103] See id. at 1494.
[104] See id. at 1496.
[105] Id. at 1496.
[106] Id.
[107] Fonovisa, 75 F.3d at 264.
[108] Which, we argue, they usually do not. See infra Section V.
[109] See Niva Elkin-Koren, Cyberlaw and Social Change: A Democratic Approach to Copyright Law in Cyberspace, 14 Cardozo Arts & Ent LJ 215, 272 n. 231 (1996) ("It is arguable that a link is very similar to a bibliography entry. It refers users of one document to other documents that may be relevant. It also provides the location of further information"). Interestingly, under U.S. defamation law it has been held that merely telling another where they may find defamatory information is not, in itself, defamation. See MacFadden v. Anthony, 117 N.Y.S.2d 520 (N.Y. Sup. Ct. 1952) (radio commentary calling attention to allegedly libelous article without repeating any of the allegedly defamatory matter was not a republication or publication of a libel). Not all jurisdictions follow this logic, though, and the opposite may be true in Germany where Berlin prosecutors recently accused a left-wing politician with telling others, through a link on her web page, where they could find an illegal publication (a felony). The specific charge was "disturbing the public peace by distributing texts which sanction dangerous offenses against the public." Yahoo News Page, (visited Feb. 28, 1998) <http://www.yahoo.com/headlines/970120/tech/stories/germany_1.html>.
[110] Sega, 948 F.Supp. at 932. See Sega v. Sabella, No. C 93-04260, 1996 WL 780560, at *8 (N.D. Cal. Dec. 18, 1996) (applying the Netcom case's "substantial participation" test).
[111] One could imagine, however, an unauthorized linking fact pattern where the linking party could defend on substantial non-infringing use grounds. For instance, some sites randomly generate a URL to which a user can link. Imagine one that did this via an auto-load or framed environment. Most of the time, because of the defenses available to the user against a direct infringement claim noted in section V, the user will not be infringing when viewing the copyrighted material on this type of site. However, even if the user's browsing of a particular page in this way was deemed an infringement based on some specific facts related to the copyrighted site at issue, at least as against a means-to-infringe claim, the linking party seems to be protected by substantial non-infringing use. That is because it seems unlikely that every URL generated by the random URL generator would result in a link to a page that, when viewed by the user, would be an infringement. (Some pages might be public domain, or specifically authorize this type of browsing, for example.) Accordingly, the instrumentality at issue (the link) has substantial non-infringing use (linking to pages where no infringement results).
[112] However, the direct infringer need not be a party to the suit, 3 M. NIMMER AND D. NIMMER, NIMMER ON COPYRIGHT §12.04[A][3][a] (1996).
[113] Sony Corp. of America v. Universal City Studios, Inc., 464 U.S. 417, 456 (1984).
[114] A third defense might revolve around the "first sale" doctrine, which gives legitimate holders of a copyrighted work latitude to sell or otherwise dispose of the physical copy to others. 17 U.S.C.A. §109(a) (West 1996). However, there are serious questions about the first sale doctrine's applicability to digital transmissions. For instance, one argument is that, since a new copy made during the electronic browsing process occurs before the old is one is deleted, the first sale probably does not apply. Johnson, supra note 44 see also Elkin-Koren, supra note 106, at 277 ("Since the first sale doctrine applies to distribution of physical copies, it remains unclear whether the doctrine applies to on-line transmission").
[115] 17 U.S.C.A. § 204(a) (1996).
[116] 17 U.S.C.A. § 101 (1996) (see the "transfer of copyright ownership" definition).
[117] Effects Associates, Inc. v. Cohen, 908 F.2d 555 (9th Cir. 1990) cert. denied, 498 U.S. 1103 (1991).
[118] 17 U.S.C.A. § 101 (West 1996); see also I.A.E., Inc. v. Shaver, 74 F.3d 768 (7th Cir. 1996) (holding that even though the statute invalidates any transfer that is not in writing, the copyright act also explicitly removes the non-exclusive license from the writing requirement).
[119] 17 U.S.C.A. § 101 (West 1996).
[120] Id.; Effects Associates, 908 F.2d at 559; Avtech Sys., Inc. v. Peiffer, 21 F.3d 568, 574 n.12 (4th Cir. 1994).
[121] See 3 M. NIMMER AND D. NIMMER, NIMMER ON COPYRIGHT, § 10.03[A] (1997).
[122] Id., § 10.03[A], n.19.
[123] I.A.E., Inc. v. Shaver, 74 F.3d at 775; Pinkham v. Sara Lee Corp., 983 F.2d 824, 831 (8th Cir. 1992) (unlike an exclusive license, an authorization can be given orally or implied from conduct.)
[124] Gracen v. Bradford Exchange, 698 F.2d 300 (7th Cir. 1983).
[125] See id. at 303.
[126] Effects Associates, 908 F.2d at 559 n.6.; I.A.E., Inc. v. Shaver, 74 F.3d 768, 776 (7th Cir. 1996).
[127] Allen-Myland v. International Business Machines Corp., 746 F.Supp. 520, 524 (E.D. Pa. 1990); Medico Security Locks, Inc. v. Locke Technology Corp., 199 U.S.P.Q. 519, 524 (S.D.N.Y. 1976).
[128] 952 F.2d 769 (3rd Cir. 1991).
[129] See id.
[130] Pam Filoff v. Giant Records, Inc., 794 F.Supp. 933 (N.D. Cal. 1992) (the court held that the Copyright Act's provision requiring a written transfer of copyright ownership was not satisfied by a recording agreement (which did not transfer any ownership rights) and an unsigned document).
[131] Silva v. MacLaine, 697 F.Supp. 1423 (E.D. Mich. 1988) (book author brought copyright action against another author of a subsequent book on similar topic; the court held that plaintiff author had granted nonexclusive oral license to use part of his book)
[132] See Lemley supra note 43.
[133] See JOHN BROCKMAN, DIGERATI 136 (1996) (quoting David Johnson). The exception to this general rule involves password protected sites such as subscription sites. However, since it would do no good for the linking party to link to such sites, as the user would not have the password, those facts are not considered here.
[134] Mai Systems Corp. v. Peak Computer, Inc., 991 F.2d 511 (9th Cir. 1993). See also Marobie-FL, Inc. v. National Assoc. of Fire Equipment Distributors, 983 F. Supp. 1167. In Marobie-FL, a WWW hosting company argued unsuccessfully that the transmission of infringing files through its system does not constitute sufficient fixation for purposes of establishing infringement. 983 F. Supp. at 1176.
[135] 17. U.S.C.A. § 117 (West 1996).
[136] See David J. Loundy, Revising the Copyright Law For Electronic Publishing, 14 J. MARSHALL J. COMPUTER & INFO. L. 1, 33-34 (1995).
[137] Id. at 34.
[138] Apple Computer v. Formula Inturn, Inc., 594 F.Supp. 617, 621 (C.D. Cal. 1984).
[139] This may be an invalid assumption, see infra note 156.
[140] For an early look at the doctrine, see EDWARD A. CAVAZOS AND GAVINO MORIN, CYBERSPACE AND THE LAW: YOUR RIGHTS AND DUTIES IN THE ON-LINE WORLD 59 (1994) (discussing the scope of implied license to materials "posted" to on-line discussion groups).
[141] See Jane C. Ginsburgh, Putting Cars on the "Information Superhighway": Authors, Exploiters and Copyright in Cyberspace, 95 Colum. L. Rev. 1466, 1477-78 (1995).
[142] Johnson, supra note 45, at 1386-87 citing Cyberspace Law Institute, Copyright Law on the Internet: The Special Problem of Caching and Copyright Protection (dated Sept. 1, 1995) <http://www.II.georgetown.edu:80/cli.html>; Pamela Samuelson, Legally Speaking: Intellectual Property Rights and the Global Information Economy, 39 COMMUN. A.C.M. 23, 26-27 (1996).
[143] See Campbell v. Acuff-Rose Music, Inc., 510 U.S. 569, 577 (1994).
[144] 17 U.S.C.A. § 107 (West 1996).
[145] Time, Inc. v. Bernard Geis Assocs., 293 F.Supp. 130, 144 (S.D.N.Y. 1968).
[146] See H.R. Rep. No. 94-1476, at 66 (1976), reprinted in 1976 U.S.C.C.A.N. 5659, 5680; S. Rep. No. 94-473, at 62 (1975) ("Section 107 is intended to restate the present judicial doctrine of fair use, not to change, narrow, or enlarge it in any way.")
[147] Ginsburgh, supra note 138, at 1480.
[148] 464 U.S. 417 (1984).
[149] See id. at 423.
[150] 149 See id.
[151] Id. at 447 n.28.
[152] See id.
[153] Id. at 449-50.
[154] See Williams & Wilkins Co. v. United States, 487 F.2d 1345 (Ct. Cl. 1973), aff'd per curiam, 420 U.S. 376 (1975) (holding personal photocopying to be non-infringing as a fair use). But see Sony, 464 U.S. at 465 (Blackmun, J., dissenting) ("neither the statute nor its legislative history suggests any intent to create a general exemption for a single copy made for personal or private use.")
[155] Religious Technology v. Netcom On-Line Communications, Inc., 907 F.Supp. 1361, 1378 n.25 (N.D. Cal. 1995).
[156] Elkin-Koren, supra note 106, 283-289 (arguing for more expansive fair use rights for individual personal use).
[157] Id.
[158] See KENT D. STUCKEY ET AL., INTERNET AND ONLINE LAW, 6-28 (1996) (citing Harper & Row Publishers, Inc. v. Nation Enterprises, 471 U.S. 539, 566-567(1985)).
[159] While the economic threat described here is undoubtedly a motivating factor behind potential unauthorized linking claims, it should be noted that other motivations might exist. The owner of a site might want to limit the number of hits to a site to prevent overloading the capacity of the WWW server from which the material is disseminated. Alternatively, a copyright owner might be inclined to make a claim involving unauthorized linking if the linking party is an entity to whom the copyright owner does not want to be associated. See generally 2 PAUL GOLDSTEIN, COPYRIGHT: PRINCIPLES, LAW AND PRACTICE § 10.2.1.2, at 208 (1989 & Supp. 1994) (noting circumstances, such as those involving parodies, where copyright owners might be reluctant to license their works).
[160] But see Campbell v. Acuff-Rose Music, Inc., 510 U.S. 569, 584 (1994) ("If, indeed, commerciality carried presumptive force against a finding of fairness, the presumption would swallow nearly all of the illustrative uses listed in the preamble paragraph of 107, including news reporting, comment, criticism, teaching, scholarship, and research, since these activities are generally conducted for profit in this country.").
[161] While the Copyright Act provides for criminal sanctions, such penalties are only available when the infringement is performed "willfully and for purposes of commercial advantage or private financial gain." 17 U.S.C.A. § 506(a)(1) (West 1996). Attempts to circumvent the Act's criminal provision, and its attendant defenses, in this context have been resoundingly rebuffed by the courts as inapplicable. See U.S. v. LaMacchia, 871 F. Supp. 535 (D. Mass. 1994) (dismissing federal wire fraud charges against defendant alleged to have been involved in software piracy); State v. Perry, Appeal No. C-960297, 1997 WL 71299 (Ohio Ct. App., Feb. 12, 1997 (holding that the sysop of a "pirate" BBS could not be prosecuted under state criminal laws as those laws are preempted by the Copyright Act).
[162] See 15 U.S.C.A. § 1114 (West 1996).
[163] See 15 U.S.C.A. § 1125(c) (West 1996).
[164] See 15 U.S.C.A. § 1125(b) (West 1996).
[165] There are two ways that a state law might be preempted, statutory preemption and constitutional preemption. Statutory preemption emanates from § 301(a) of the copyright Act, which sets out three requirements, all of which must be satisfied, in order to deem a state intellectual property law preempted. First, the state right under scrutiny must be "equivalent to any of the exclusive rights within the general scope of copyright as specified by section 106." 17 U.S.C.A. § 301(a) (West 1996). Courts find that a state right is equivalent, and the first requirement satisfied, if (1) the right is within the scope of one or more of the exclusive rights listed in section 106, and (2) the state law requires proof of nothing more than the Act requires to prove infringement of one of those exclusive rights. Computer Assoc. Int'l, Inc. v. Altai, Inc., 982 F.2d 693, 716 (2d Cir. 1992). Second, the particular work to which the state law claim is being applied must fall within the type of works protected by the Act under §§ 102 and 103. 117 U.S.C.A. § 301(a) (West 1996).
Constitutional preemption under the U.S. Constitution's Supremacy Clause, Article VI, occurs when a state law conflicts with the federal statutory scheme in such a way as to make it impossible to comply with both laws (state and federal) or if the state law operates as an obstacle to the accomplishment of the "full purposes and objectives of Congress." California Fed. Sav. & Loan Ass'n v. Guerra, 479 U.S. 272, 281 (1987).
For an interesting discussion of these two types of preemption, the reader is invited to read Professor Mark Lemley's amicus brief (prepared for the American Committee for Interoperable Systems) in the ProCD, Inc. v. Zeidenberg, 86 F.3d 1447 (7th Cir. 1996). Appellees Amicus Brief available in <http://www.complaw.com/lawlibrary/brief.html>.
[166] 15 U.S.C.A. § 1114(1) (West 1996).
[167] See Dorr-Oliver, Inc. v. Fluid-Quip, Inc., 94 F.3d 376 (7th Cir. 1996).
[168] See McGraw-Edison v. Walt Disney Prod., 787 F.2d 1163, 1167-68 (7th Cir. 1986).
[169] 15 U.S.C.A. § 1115(b)(4) (West 1996).
[170] Soweco, Inc. v. Shell Oil Co., 617 F.2d 1178, 1185 (5th Cir.1980); William R. Warner & Co. v. Eli Lilly & Co., 265 U.S. 526, 529 (1924).
[171] See Car-Freshner Corp. v. S.C. Johnson & Son, Inc., 70 F.3d 267, 269 (2nd Cir. 1995); Sands, Taylor & Wood Co. v. Quaker Oats Co., 978 F.2d 947, 951 (7th Cir. 1992).
[172] See 15 U.S.C.A. § 1115(b)(4) (West 1996).
[173] Union Carbide Corp. v. Ever-Ready Inc., 531 F.2d 366, 379 (7th Cir.1976) (quoting A. SEIDEL, S. DALROFF AND E. GONDA, TRADEMARK LAW & PRACTICE, § 4.06 at 77 (1963)).
[174] See Forum Corp. v. Forum, Ltd., 903 F.2d 434, 444 (7th Cir. 1990)
[175] G. Heileman Brewing Co. v. Anheuser-Busch, Inc., 873 F.2d 985, 994 (7th Cir. 1989).
[176] New Kids on the Block v. New America Pub., Inc., 971 F.2d 302 (9th Cir. 1992).
[177] Id. at 308. See also Patmont Motor Works Inc. v. Gateway Marine Inc., No. C 96-2703 THE, 1997 WL 81770 (N.D. Cal. Dec. 18, 1997)(holding that use of the plaintiff's trademark in a URL constituted nominative fair use).
[178] 15 U.S.C.A. § 1125(c) (West 1996).
[179] An interpretive problem concerning the Dilution Act, viz à viz the requirement of actual confusion versus the likelihood of confusion required under many state statutes, is highlighted by the recent decision in Intermatic Inc. v. Toeppen, 947 F.Supp. 1227 (N.D. Ill. 1996). Plaintiff Intermatic sold electrical and electronic products under federally registered trademarks. Defendant Toeppen registered the domain name "intermatic.com." Intermatic sued Toeppen for trademark infringement, trademark dilution, and unfair competition. While the court correctly cited the Dilution Act in stating that a trademark owner is entitled to injunctive relief if the defendant's commercial use "causes dilution" of their famous mark (Intermatic, 947 F.Supp. at 1237-38, emphasis added), the court then held that a federal cause of action requires only that the plaintiff show the defendant's use is likely to cause dilution (Id. at 1238, emphasis added). This holding evidences a clear misreading and misunderstanding of the standard required by the Dilution Act ("actual dilution"), substituting in its stead the less stringent standard ("likelihood of confusion") contained in many state anti-dilution acts.
[180] H.R.Rep. 104-374, at , 7-83 (1995), reprinted in 1995 U.S.C.C.A.N. 1029, 1034-1035.
[181] 15 U.S.C.A. § 1127 (West 1996).
[182] H.R.Rep. 104-374, at 3, 6 (1995), reprinted in 1995 U.S.C.C.A.N. 1029, 1033.
[183] See Hormel Foods Corp. v. Jim Henson Prods., Inc., 73 F.3d 497, 506 (2d Cir. 1996) (under the New York antidilution statute, likelihood of dilution can be established by a showing either of blurring or tarnishment); Deere & Co. v. MTD Prods., Inc., 41 F.3d 39, 41 (2d Cir. 1994) (advertiser's alteration of competitor's trademark in comparative advertising was a violation of New York's antidilution statute, in that the altered mark created risk that consumers would come to attribute unfavorable characteristics to mark and ultimately associate mark with inferior goods and services).
[184] See Hormel, 73 F.3d at 507.
[185] Deere v. MTD Products, 41 F.3d 39, 43 (2d Cir. 1994).
[186] It is noted that as of March 1997, the TotalNEWS site does not employ graphic trademarks from other news sources, using instead text wording to construct their remote invoke-to-load links. See TotalNEWS' Home Page (visited Feb. 28, 1998) <http://www.totalnews.com/>.
[187] See 15 U.S.C.A. § 1125(a) (West 1996).
[188] See id. at 1125(a)(1)(a).
[189] Id. at 1125(a)(1)(b).
[190] See Dallas Cowboys Cheerleaders, Inc. v. Pussycat Cinema, Ltd., 604 F.2d 200 (2nd Cir. 1979) (the court prohibited defendants (Pussycat Cinema) from distributing or exhibiting the film "Debbie Does Dallas," a film featuring a performer in a uniform strikingly similar to one worn by plaintiff's cheerleading group, and that the association resulted in confusion which had a tendency to impugn plaintiff's services and injure plaintiff's business reputation).
[191] See, e.g., CBS, Inc. v. Springboard Intern. Records, 429 F.Supp. 563, 566 (S.D.N.Y. 1976).
[192] See Warner Brothers, Inc. v. Gay Toys, Inc., 658 F.2d 76, 78 (2nd Cir. 1982); New West Corp. v. NYM Co. of California, Inc., 595 F.2d 1194, 1198 (9th Cir. 1979).
[193] Digital Equipment Corp. v. Altavista Technology, Inc., 960 F. Supp. 456, 461(D. Mass. 1997).
[194] See, e.g., International News Serv. v. Associated Press, 248 U.S. 215 (1918).
[195] See, e.g., Sears, Roebuck & Co. v. Stiffel Co., 376 U.S. 225, 231-2, reh'g denied, 376 U.S. 973 (1964) (holding that states cannot create rights protecting objects falling under Congress' copyright and patent power, but failing to qualify for federal protection under the copyright and patent statutes); Compco Corp. v. Day-Brite Lighting, Inc., 376 U.S. 234, 237, reh'g denied, 377 U.S. 913 (1964) (holding that when an article is unprotected by federal patent or a copyright law, a state law may not forbid others from copying that article); Hoehling v. Universal City Studios, Inc., 618 F.2d 972, 980 (2nd Cir. 1980), cert. denied, 449 U.S. 841 (1980) (holding that under the constitutional preemption doctrine, state law can not protect facts).
[196] See, e.g., Goldstein v. California, 412 U.S. 546, 559, reh'g denied, 414 U.S. 883 (1973) (ruling that states can protect subject matter coming under the constitutional provision for copyrights, but falling outside the scope of the 1976 Copyright Act); Harper & Row, Publishers, Inc., v. Nation Enters., 723 F.2d 195, 200 (2nd Cir. 1983), rev'd on other grounds, 471 U.S. 539 (1985) (where state law right "is predicated upon an act incorporating elements beyond mere reproduction or the like, the [federal and state] rights are not equivalent", thereby avoiding preemption); Universal City Studios, Inc. v. Kamar Indus., Inc., 217 U.S.P.Q. 1162 (S.D. Tex. 1982) ("Generally the same facts that would support a claim for trademark infringement or common law unfair competition will support an action under Section 43(a)). But see Nat'l Basketball Assoc. v. Motorola, 105 F.3d 841 (2d Cir. 1997), cited infra note 197 and accompanying text.
[197] 304 U.S. 64 (1938) (holding that there is no general federal common law).
[198] 248 U.S. 215 (1918).
[199] See id. at 240.
[200] See id. at 231.
[201] Id. at 240.
[202] See, e.g., Metropolitan Opera Assoc. v. Wagner-Nichols Recorder Corp., 101 N.Y.S.2d 483 (N.Y. Sup. Ct. 1950), aff'd, 107 N.Y.S.2d 795 (1951) (plaintiff Metropolitan Opera granted injunction against defendant for unfair competition, where defendant recorded plaintiff's radio broadcast performances and made and sold phonograph records thereof); Gilmore v. Sammons, 269 S.W. 861 (Tex.Civ.App. -Dallas 1925, writ ref'd) (court held Sammons' taking of news items from Gilmore's paper and republishing same constituted an unfair and illegal interference with Gilmore's business).
[203] 105 F.3d 841 (2d Cir. 1997).
[204] See id. at 844.
[205] See id. at 845.
[206] See U.S. CONST. art. VI ("This Constitution, and the Laws of the United States . . . shall be the supreme Law of the Land").
[207] 2 PAUL GOLDSTEIN, COPYRIGHT: PRINCIPLES, LAW, PRACTICE, II, § 15.3.3 (1989 & Supp. 1994).
[208] See Computer Associates Int'l, Inc. v. Altai, Inc., 982 F.2d 693, 711 (2d Cir. 1992) ("The interest of the copyright law is not in simply conferring a monopoly on industrious persons, but in advancing the public welfare through rewarding artistic creativity, in a manner that permits the free use and development of non-protectable ideas and processes.").
[209] International News Service v. Associated Press, 248 U.S. 215, 239-40 (1918).
[210] See 15 U.S.C.A. 1125(a) (West 1996).
[211] See Hudgens v. Goen, 673 S.W.2d 420, 423 (Tex. Ct. App. -Fort Worth 1984, writ ref'd n.r.e.).
[212] Boston Prof'l Hockey Ass'n, Inc. v. Dallas Cap & Emblem Mfg., Inc., 510 F.2d 1004, 1010 (5th Cir.), cert. denied 423 U.S. 868 (1975).
[213] See ProCD, Inc. v. Zeidenberg, 86 F.3d 1447 (7th Cir. 1996) (the court held that a software shrinkwrap license is binding on the software's purchaser and that enforcement of such a license under state law was not preempted by Copyright Act).
[214] See id. at 1449 ("shrinkwrap licenses are enforceable unless their terms are objectionable on grounds applicable to contracts in general[,] for example, if they violate a rule of positive law, or if they are unconscionable"). But see Mark A. Lemley, Shrinkwraps in Cyberspace, 35 JURIMETRTICS J. 311 (1995) (questioning the validity of shrinkwrap licenses).
[215] This assumes that the unauthorized link is to a page that contains the disclaimer.
[216] M. ETHAN K ATSH, LAW IN A DIGITAL WORLD 226 (1994).
[217] Katsh, supra note 215, at 226.
[218] See Raymond T. Nimmer and Patricia Ann Krauthaus, Information as Property: Databases and Commercial Property, 1 OXFORD J.L. & INFO. TECH. 1, 32 (1993) ("the rights to control (and charge for) access to, and use of, information are the critical variables, rather than a right to control the making of copies").
[219] See Rebecca Quick, 'Framing' Muddies Issue Of Content Ownership, W ALL ST. J., Jan. 30, 1997, at B10.
[220] See, e.g., I. Trotter Hardy, The Proper Legal Regime for "Cyberspace", 55 U. PITT. L. REV. 993 (1994); Robert L. Dunne, Deterring Unauthorized Access to Computers: Controlling Behavior in Cyberspace Through a Contract Law Paradigm, 35 Jurimetrics J. 1 (1994).
[221] See Elkin-Koren, supra note 107; Julie E. Cohen, A Right to Read Anonymously: A Closer Look at Copyright Management in Cyberspace, 28 C ONN. L. REV. 981 (1996).